
The Long Term Evolution mobile device standard used by billions of people was designed to fix many of the security shortcomings in the predecessor standard known as Global System for Mobile communications. Mutual authentication between end users and base stations and the use of proven encryption schemes were two of the major overhauls. Now, researchers are publicly identifying weaknesses in LTE that allow attackers to send nearby users to malicious websites and fingerprint the sites they visit.
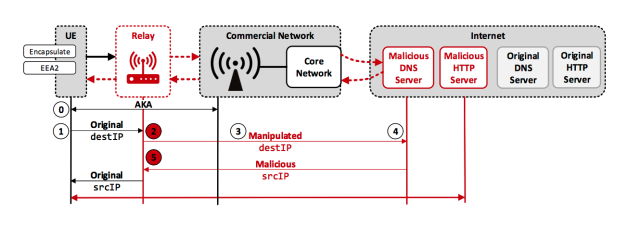
The attacks work because of weaknesses built into the LTE standard itself. The most crucial weakness is a form of encryption that doesn’t protect the integrity of the data. The lack of data authentication makes it possible for an attacker to surreptitiously manipulate the IP addresses within an encrypted packet. Dubbed aLTEr, the researchers’ attack causes mobile devices to use a malicious domain name system server that, in turn, redirects the user to a malicious server masquerading as Hotmail. The other two weaknesses involve the way LTE maps users across a cellular network and leaks sensitive information about the data passing between base stations and end users.
Well-known attack vectors
The attacks, which are described in a paper published Thursday, require about $4,000 worth of equipment that must be within about one mile of the targeted user. Because the weaknesses are the result of design decisions made when the LTE specification was under development, there is no way to patch them now. End users, however, can protect themselves against aLTEr by only visiting websites that use HTTP Strict Transport Security and DNS Security Extensions.
In an email, researchers Thorsten Holz and David Rupprecht of the Ruhr-Universität Bochum wrote:
The two significant contributions are that we show that LTE suffers from several attack vectors and demonstrate that LTE is vulnerable in practice. Most importantly, the aLTEr attack enables an adversary to redirect network connections and thus perform several kinds of attacks. Note that the underlying attack vectors are well-known and such attacks were demonstrated in other kinds of protocols in the past. We are the first to demonstrate that LTE, despite a lot of security improvements compared to GSM, also suffers from such attacks. We hope that our research will influence the security-related decisions in 5G such that future mobile communication protocols are not vulnerable to such attacks.
Note that an attacker that wants to perform our attacks still needs to be in the proximity of the victim and she required special equipment (although this is easily available for an attacker). We think that, in particular, people that are of special interest (politicians, journalists, ambassadors, upper management, …) should care about such attacks (see for example the attacks against politicians uncovered via the Snowden leaks). The main consequences of our attacks are that an attacker can use them to redirect network traffic, determine the visited website, or use this attack as a stepping stone for further attacks.
An overview of the aLTEr attack is below:
Rupprecht et al.
Here’s a video of the attack:
[embedded content]
Demonstration of the aLTEr attack in a commercial LTE network
The GSM Association, which represents almost 800 mobile operators and more than 300 hardware and software companies, is already aware of the weaknesses. In an emailed statement, GSMA officials wrote:
Although LTE user traffic is encrypted over the radio interface and cannot be eavesdropped, it is not integrity protected. The research has shown that this lack of integrity protection can be exploited in certain circumstances using sophisticated radio equipment to modify user traffic. For example, when a user attempts to connect to a website that does not enforce the use of the HTTPS security protocol, the researchers have shown that it can be possible to re-direct users to a fake website.
Although the researchers have shown traffic modification to be feasible in a laboratory environment, there are a number of technical challenges to make it practical outside a laboratory. Mobile operators have fraud detection functions that can detect and react to certain attack scenarios, while several mobile applications and services use enforced HTTPS, which prevents traffic modification.
The GSMA does not believe that the specific technique demonstrated by the researchers has been used to target users in the past, nor is it likely to be used in the near future. However, as a result of this new research, the GSMA is working with the industry to investigate how to include the protection of the integrity of traffic and information (user plane integrity) in LTE. The 5G standards already include support for user plane integrity protection, and the GSMA is supporting the industry to ensure that it is fully deployed as 5G technology rolls out.
Officials with the 3rd Generation Partnership Project, which also oversees the LTE specification, didn’t immediately respond to an email seeking comment for this post.
In an informational website about the vulnerabilities, the researchers said that the attacks would be hard—but by no means impossible—to pull off on an operational LTE network. An attacker would need software-defined radios that run a customized implementation of the LTE specification. Attackers would also have to devise ways to make the connection stable, filter out radio interference, and evade fraud detection software implemented by many network operators. An attacker would also be required to know in advance where a target is located and have a malicious base station operating within a mile of the location.
Holz and Rupprecht said the 5G specification that’s slated to replace LTE has the ability to mitigate the weaknesses by using what’s known as user plane integrity protection. That protection, however, is optional and requires that an operator use specific equipment. The researchers are suggesting that the 5G specification be revised to make integrity assurance mandatory.
“Based on our findings,” the researchers wrote, “we urgently demand the implementation of effective countermeasures in the upcoming 5G specification to assure the security and privacy of future mobile communication.”
Be the first to comment