For their entire existence, some of the world’s most widely used email encryption tools have been vulnerable to hacks that allowed attackers to spoof the digital signature of just about any person with a public key, a researcher said Wednesday. GnuPG, Enigmail, GPGTools, and python-gnupg have all been updated to patch the critical vulnerability. Enigmail and the Simple Password Store have also received patches for two related spoofing bugs.
Digital signatures are used to prove the source of an encrypted message, data backup, or software update. Typically, the source must use a private encryption key to cause an application to show that a message or file is signed. But a series of vulnerabilities dubbed SigSpoof makes it possible in certain cases for attackers to fake signatures with nothing more than someone’s public key or key ID, both of which are often published online. The spoofed email shown at the top of this post can’t be detected as malicious without doing forensic analysis that’s beyond the ability of many users.
Backups and software updates affected, too
The flaw, indexed as CVE-2018-12020, means that decades’ worth of email messages many people relied on for sensitive business or security matters may have in fact been spoofs. It also has the potential to affect uses that went well beyond encrypted email.
“The vulnerability in GnuPG goes deep and has the potential to affect a large part of our core infrastructure,” Marcus Brinkmann, the software developer who discovered SigSpoof, wrote in an advisory published Wednesday. “GnuPG is not only used for email security but also to secure backups, software updates in distributions, and source code in version control systems like Git.”
CVE-2018-12020 affects vulnerable software only when it enables a setting called verbose, which is used to troubleshoot bugs or unexpected behavior. None of the vulnerable programs enables verbose by default, but a variety of highly recommended configurations available online—including the cooperpair safe defaults, Ultimate GPG settings, and Ben’s IT-Kommentare—turn it on. Once verbose is enabled, Brinkmann’s post includes three separate proof-of-concept spoofing attacks that work against the previously mentioned tools and possibly many others.
The spoofing works by hiding metadata in an encrypted email or other message in a way that causes applications to treat it as if it were the result of a signature-verification operation. Applications such as Enigmail and GPGTools then cause email clients such as Thunderbird or Apple Mail to falsely show that an email was cryptographically signed by someone chosen by the attacker. All that’s required to spoof a signature is to have a public key or key ID.
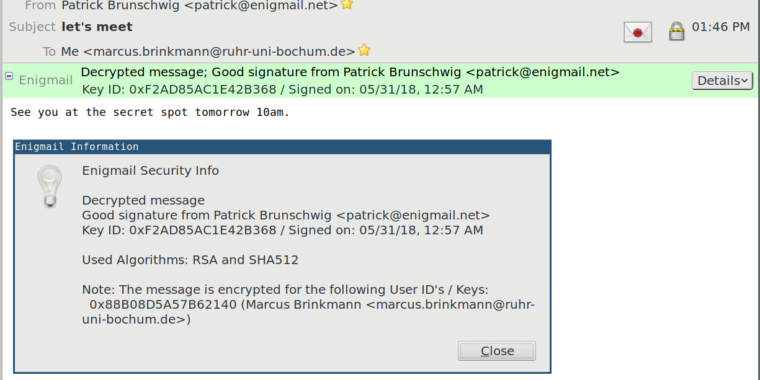
The attacks are relatively easy to carry out. The code for one of Brinkmann’s PoC exploits that forges the digital signature of Enigmail developer Patrick Brunschwig is:
$ echo 'Please send me one of those expensive washing machines.' | gpg --armor -r VICTIM_KEYID --encrypt --set-filename "`echo -ne '' n[GNUPG:] GOODSIG DB1187B9DD5F693B Patrick Brunschwig n[GNUPG:] VALIDSIG 4F9F89F5505AC1D1A260631CDB1187B9DD5F693B 2018-05-31 1527721037 0 4 0 1 10 01 4F9F89F5505AC1D1A260631CDB1187B9DD5F693B n[GNUPG:] TRUST_FULLY 0 classic ngpg: ''`" > poc1.msg
A second exploit is:
echo "See you at the secret spot tomorrow 10am." | gpg --armor --store --compress-level 0 --set-filename "`echo -ne '' n[GNUPG:] GOODSIG F2AD85AC1E42B368 Patrick Brunschwig n[GNUPG:] VALIDSIG F2AD85AC1E42B368 x 1527721037 0 4 0 1 10 01 n[GNUPG:] TRUST_FULLY n[GNUPG:] BEGIN_DECRYPTION n[GNUPG:] DECRYPTION_OKAY n[GNUPG:] ENC_TO 50749F1E1C02AB32 1 0 ngpg: ''`" > poc2.msg
Brinkmann told Ars that the root cause of the bug goes back to GnuPG 0.2.2 from 1998, “although the impact would have been different then and changed over time as more apps use GPG.” He publicly disclosed the vulnerability only after developers of the tools known to be vulnerable were patched. The flaws are patched in GnuPG version 2.2.8, Enigmail 2.0.7, GPGTools 2018.3, and python GnuPG 0.4.3. People who want to know the status of other applications that use OpenPGP should check with the developers.
Wednesday’s vulnerability disclosure comes a month after researchers revealed a different set of flaws that made it possible for attackers to decrypt previously obtained emails that were encrypted using PGP or S/MIME. Efail, as the bugs were dubbed, could be exploited in a variety of email programs, including Thunderbird, Apple Mail, and Outlook.
Separately, Brinkmann reported two SigSpoof-related vulnerabilities in Enigmail and the Simple Password Store that also made it possible to spoof digital signatures in some cases. CVE-2018-12019 affecting Enigmail can be triggered even when the verbose setting isn’t enabled. It, too, is patched in the just-released version 2.0.7. CVE-2018-12356, meanwhile, let remote attackers spoof file signatures on configuration files and extensions scripts, potentially allowing the accessing of passwords or the execution of malicious code. The fix is here.
Be the first to comment