
For more than a year, Mozilla Firefox and Google Chrome may have leaked users’ Facebook usernames, profile pictures, and likes if the users’ browsers visited malicious websites that employed a cutting-edge hack, researchers said Thursday.
The data could be extracted through what’s known as a side-channel vulnerability in the browsers’ implementation of new standards for cascading style sheets introduced in 2016. One of the new features known as the “mix-blend-mode” leaked visual content hosted on Facebook to websites that included an iframe linking to it and some clever code to capture the data. Normally, a security concept known as the same-origin policy forbids content hosted on one domain to be available to a different domain. The vulnerability was significant because it allowed hackers to bypass this bedrock principle for two of the Internet’s most widely used browsers.
The leak was independently discovered by two different research teams, and it was fixed late last year in version 63 of Chrome and two weeks ago in Firefox 60. While the updated browsers no longer pose a threat to user privacy, one of the researchers who discovered the vulnerability said the increasingly powerful graphics capabilities being added in the HTML5 and CSS standards are likely to make similar hacks possible in the future.
More to come
“CSS, HTML, and JavaScript have lots of different features to do graphical stuff,” independent researcher Dario Weißer told Ars. “I wouldn’t be surprised if there are similar, yet unknown, issues.”
Along with researcher Ruslan Habalov, Weißer developed a proof-of-concept exploit that allowed websites to extract the Facebook usernames, profile pictures, and likes of Chrome and Firefox users who visited while they were logged in to Facebook. The PoC used an iframe that linked to social plugins Facebook makes available for websites to display the Facebook login button and like button on their pages. While the same-origin policy prevented the PoC from accessing the Facebook HTML and other coding, the exploit was able to use the mix-blend-mode function to infer those details from the images hosted in the Facebook plugins.
Weißer explained:
We cannot access the iframe’s content directly. However, we can put overlays over the iframe that do some kind of graphical interaction with the underlying pixels. Since these overlays are controlled by the attacker’s site, it is possible to measure how long these graphical interactions take. Some of the mix-blend-modes require a variable amount of time based on the color of the underlaying pixel. If the color of the tested pixel has color X, the rendering process can take longer than for color Y. The leak allows [us to] determine the color of individual pixels. We don’t leak the HTML, but the visual contents of the targeted iframe.
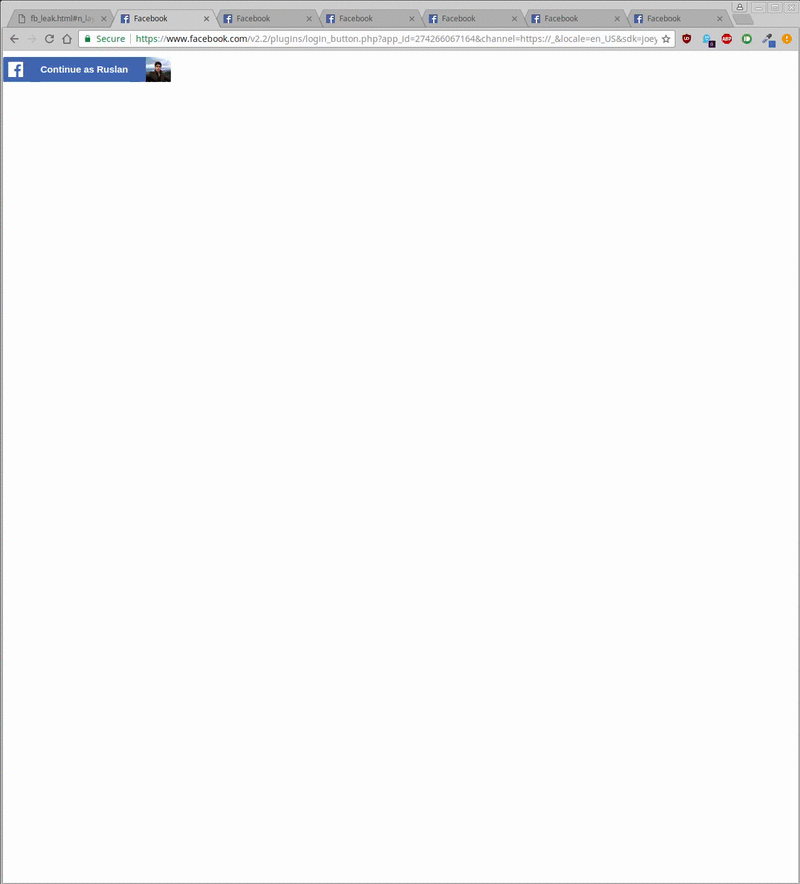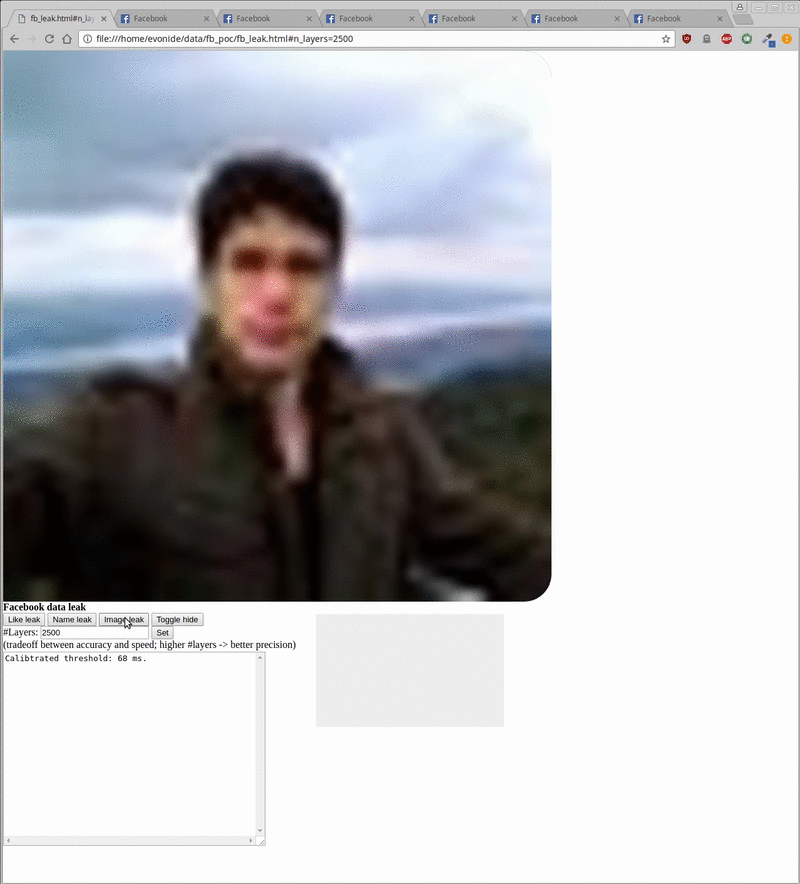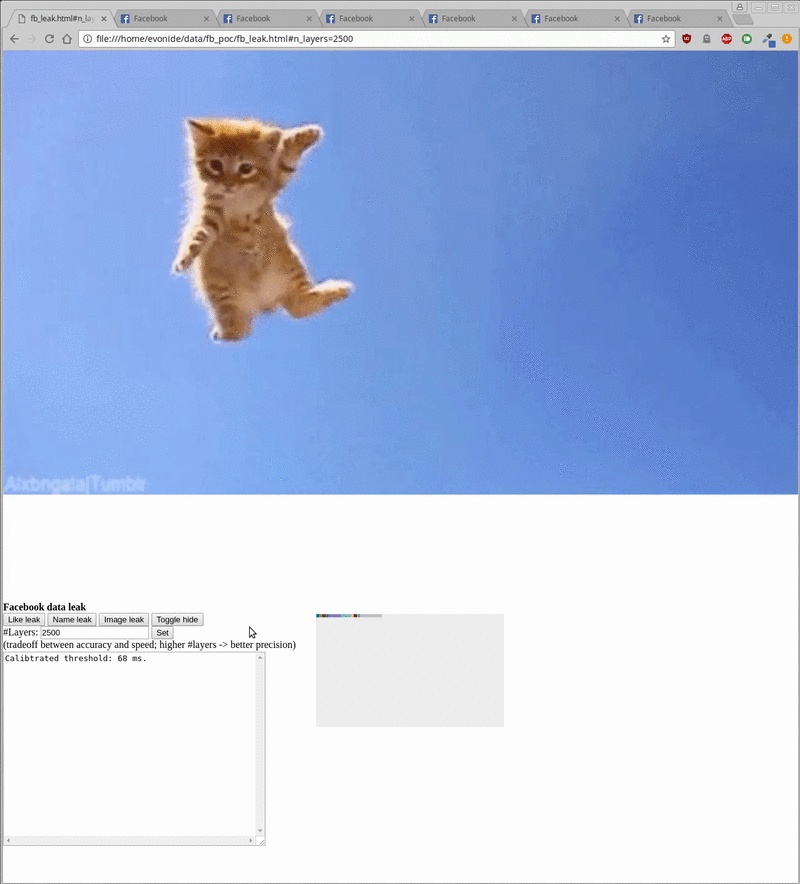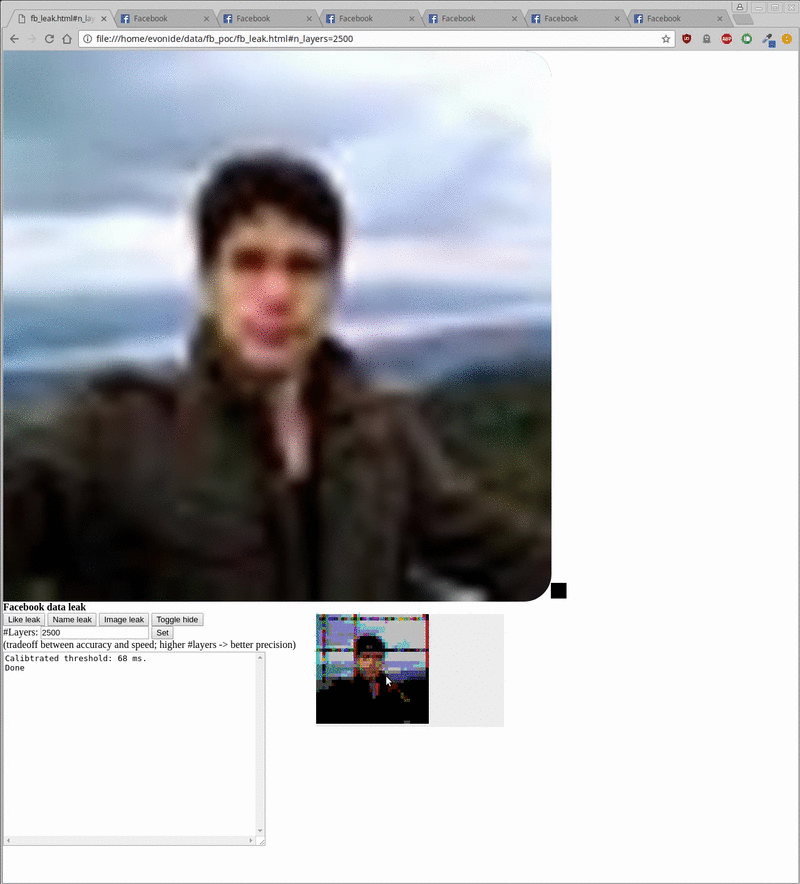
By retrieving the colors of each pixel, attackers can infer the image and then manually inspect it or use optical character-recognition techniques to read the words displayed in the images. The PoC needed less than one second to check the like status for a given website, 20 seconds to extract a visitor’s user name, and five minutes to extract a crude rendering of the visitor’s profile picture.
The following images show how the extraction worked:
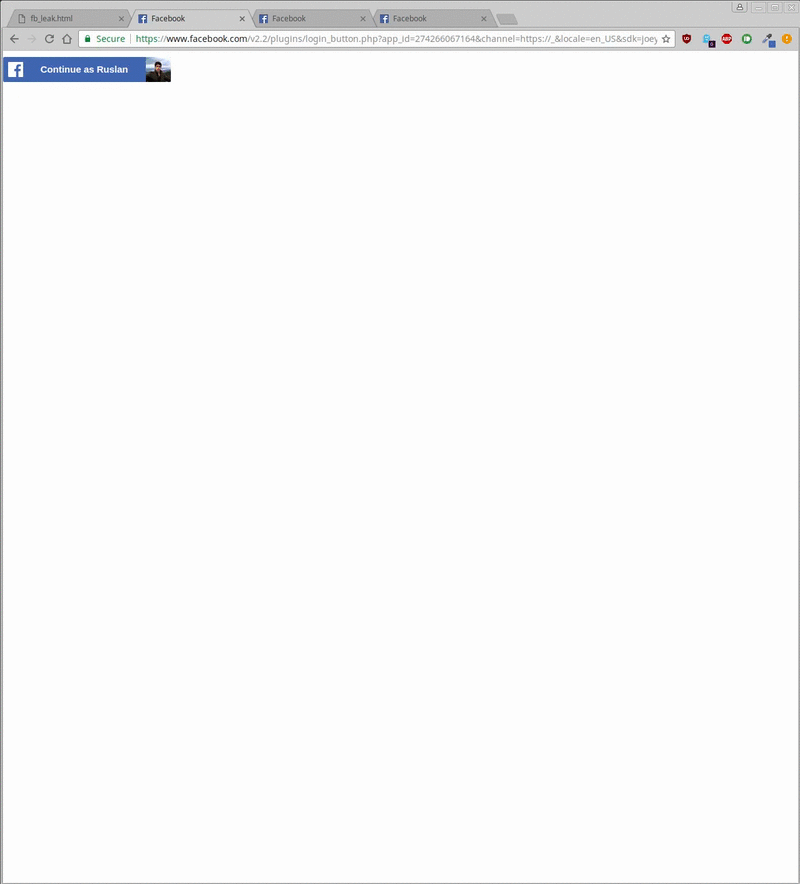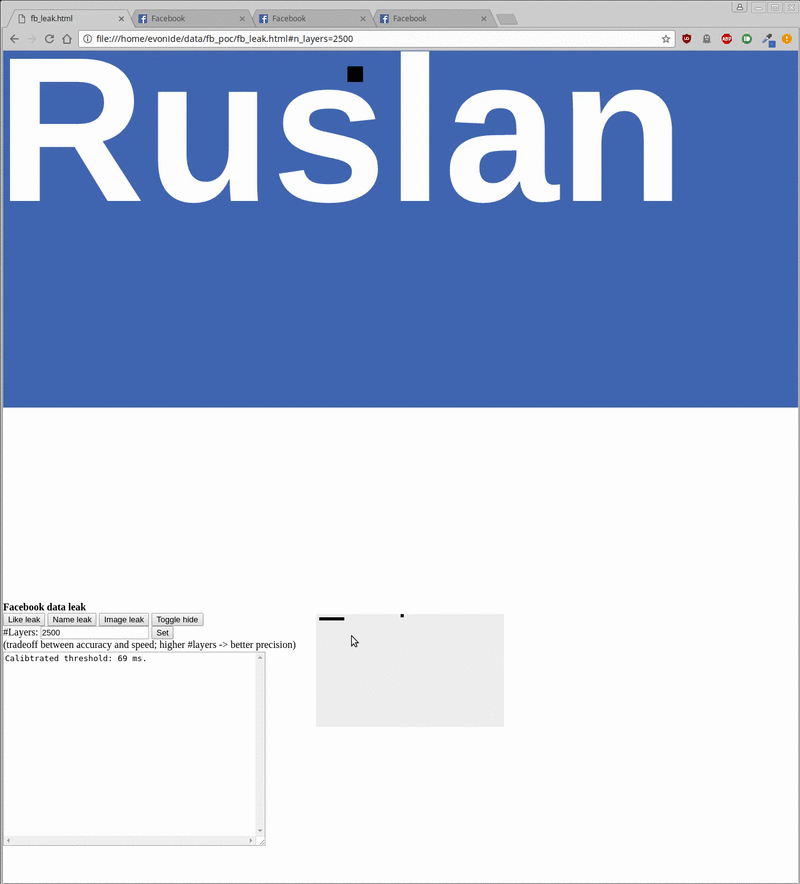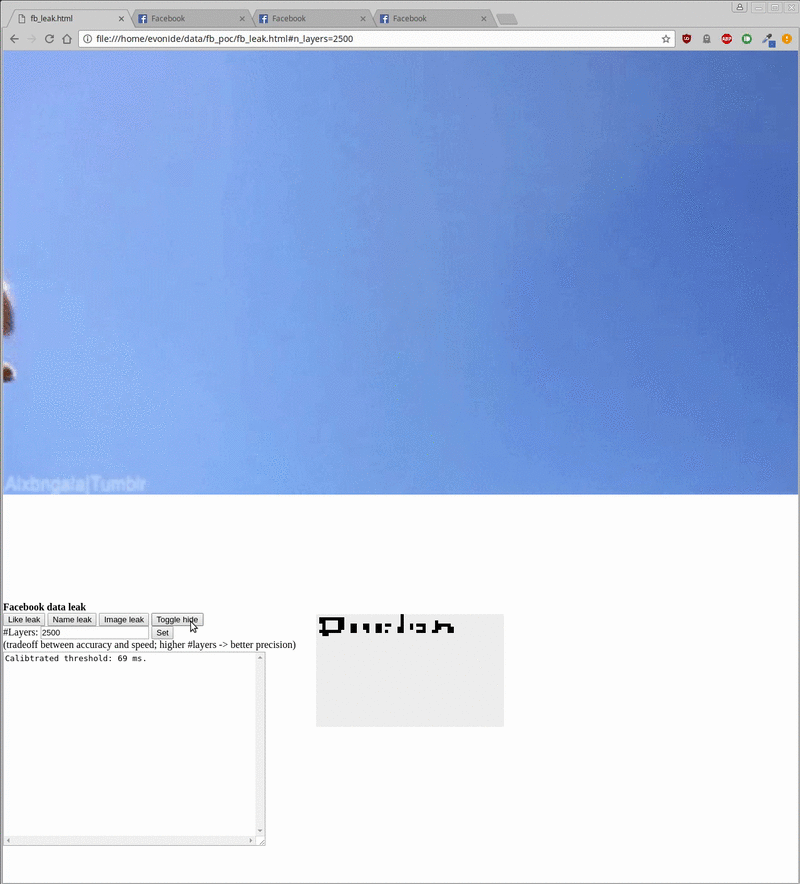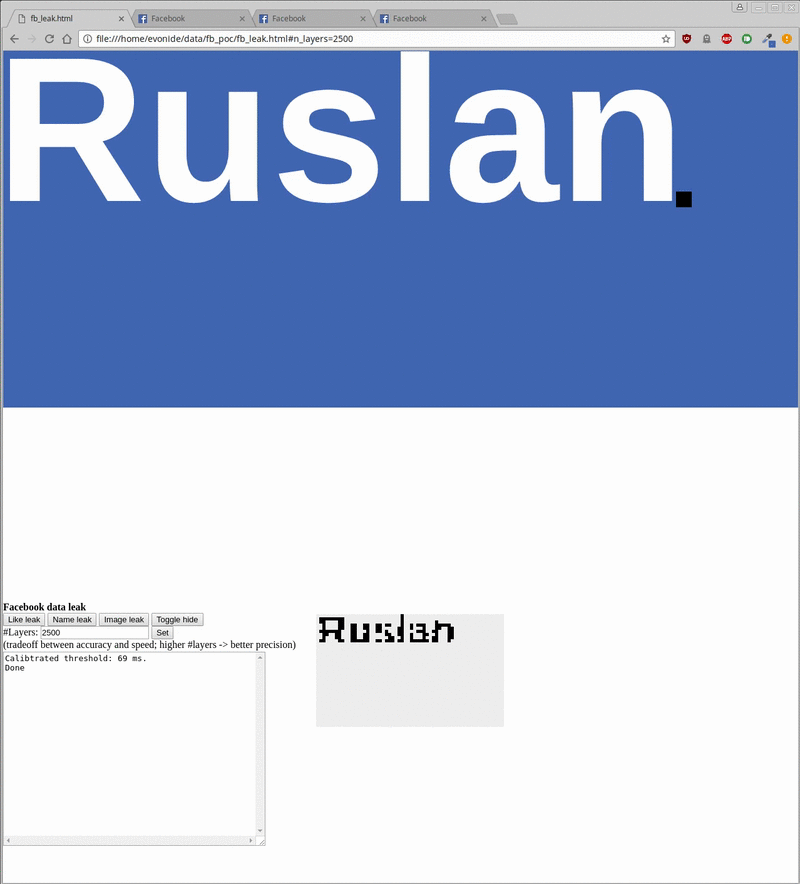
Ruslan Habalov
Ruslan Habalov
By the time Weißer and Habalov discovered the side chanel in April 2017, a separate researcher named Max May had already reported it on the Chromium mail list, unbeknownst to Weißer and Habalov. Weißer and Habalov privately reported the vulnerability to Facebook, Google, and makers of the Skia graphics library that Chrome uses. Skia patched the flaw the same month, and Google issued a patch in December.
Facebook, meanwhile, said it was infeasible to patch the vulnerability. Because of an error, Weißer and Habalov didn’t notify Mozilla of the flaw until November 2017, a lapse that explains why a Firefox fix wasn’t available until two weeks ago.
Weißer said Internet Explorer and Edge weren’t affected because they didn’t implement mix-blend-mode. He said Safari was also unaffected, but he wasn’t sure why. While this bug is fixed and probably didn’t affect many sites beyond Facebook, similar browser flaws that have yet to be publicly disclosed likely affect other properties.
“We have only demonstrated the attack potential against Facebook,” Habalov wrote in a blog post that explains the side-channel exploit in detail. “However, throughout the Web, there are tons of other sensitive resources which could be affected by attacks like this in a similar fashion. Unfortunately, we anticipate more and more of such vulnerabilities to be discovered over the years to come.”
Be the first to comment