It just got much easier to wage distributed denial-of-service attacks of once-unthinkable sizes, thanks to the public release of two ready-to-run exploits that abuse poorly secured memcached servers to flood targets with record amounts of junk traffic.
As Ars reported last week, DDoSers last month started bouncing specially developed traffic off of so-called memcached servers, which then respond by bombarding a targeted third party with a malicious flood that’s thousands of times the size of the original payload. Attackers have long used such amplification techniques to magnify or augment the damage coming from the computers they control. What’s special about memcached-based attacks is the size of the amplification—as much as 51,000 times, compared with about 50 to 60 fold for techniques seen previously. The attacks work by sending requests to servers that leave open port 11211 and adding spoofed packet headers that cause the responses to be sent to the target.
Within days of the new technique going public, security firms reported it being used in a record-setting 1.3 terabit-per-second DDoS against Github and then, two days later, a record-topping 1.7 Tbps attack against an unnamed US-based service provider.
Now, two separate exploits are available that greatly lower the bar for waging these new types of attacks. The first one, called Memcrashed, prompts a user to enter the IP address to be targeted. It then automatically uses the Shodan search engine to locate unsecured memcached servers and abuses them to flood the target. Here’s a screenshot showing the interface:
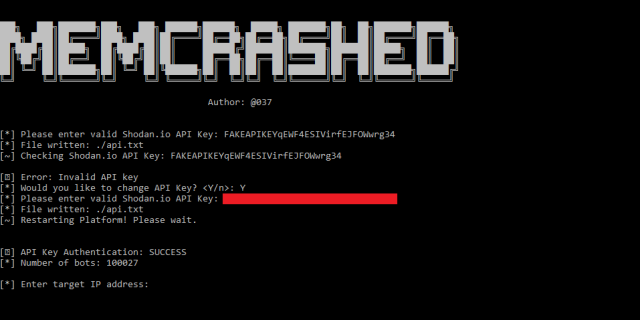
The second published exploit relies on this static list of 17,000 unsecured memcached servers to wage assaults against targets. At the time this post went live, the list was last updated on Tuesday.
Drawing attention
Memcrashed has a two-second delay built in to the code that prevents it from being used to wage the types of record-breaking attacks seen recently in the wild. But it wouldn’t be hard for someone to bypass that rate limit if she wanted to use the code to deliver malicious attacks, the exploit writer, Amir Khashayar Mohammadi, told Ars.
“That, however, is not my intent,” Mohammadi wrote in an email. “My intent is to draw more attention to the problem here. That way vendors that own these servers can take them off the Internet or at least close port 11211 or disable UDP. My intention was never to code something to be used maliciously, hence why I released the code a week after the vulnerability was spotted (a grace period in my books).”
Memcached is an open source, distributed memory-caching system that’s designed to speed up websites and cloud networks. Security professionals have noted since last week that the failure of administrators to properly secure roughly 93,000 such servers poses a threat to the stability of the entire Internet. Much of the inertia in fixing the problem is the result of the comparative lack of harm posed to the memcached servers. While the attacks have the potential to consume the bandwidth and computing resources of open servers, those negative effects are significantly less than those visited on the targeted servers on the receiving end.
Service providers that still permit spoofed data packets to traverse their networks also play a crucial role in allowing amplification attacks, but once again the providers aren’t significantly harmed, either. Without a strong incentive to change, these practices may continue unabated for weeks or months.
Be the first to comment