A digital signature used by malware that infected the network of Kaspersky Lab in 2014. Counterfeit certificates that generate such fraudulent signatures are being sold online for use in other malware.
Kaspersky Lab
The Stuxnet worm that targeted Iran’s nuclear program almost a decade ago was a watershed piece of malware for a variety of reasons. Chief among them, its use of cryptographic certificates belonging to legitimate companies to falsely vouch for the trustworthiness of the malware. Last year, we learned that fraudulently signed malware was more widespread than previously believed. On Thursday, researchers unveiled one possible reason: underground services that since 2011 have sold counterfeit signing credentials that are unique to each buyer.
In many cases, the certificates are required to install software on Windows and macOS computers, while in others, they prevent the OSes from displaying warnings that the software comes from an untrusted developer. The certificates also increase the chances that antivirus programs won’t flag previously unseen files as malicious. A report published by threat intelligence provider Recorded Future said that starting last year, researchers saw a sudden increase in fraudulent certificates issued by browser- and operating system-trusted providers that were being used to sign malicious wares. The spike drove Recorded Future researchers to investigate the cause. What they found was surprising.
“Contrary to a common belief that the security certificates circulating in the criminal underground are stolen from legitimate owners prior to being used in nefarious
campaigns, we confirmed with a high degree of certainty that the certificates are created for a specific buyer per request only and are registered using stolen corporate identities, making traditional network security appliances less effective,” Andrei Barysevich, a researcher at Recorded Future, reported.
Barysevich identified four such sellers of counterfeit certificates since 2011. Two of them remain in business today. The sellers offered a variety of options. In 2014, one provider calling himself C@T advertised certificates that used a Microsoft technology known as Authenticode for signing executable files and programming scripts that can install software. C@T offered code-signing certificates for macOS apps as well. His fee: upwards of $1,000 per certificate.
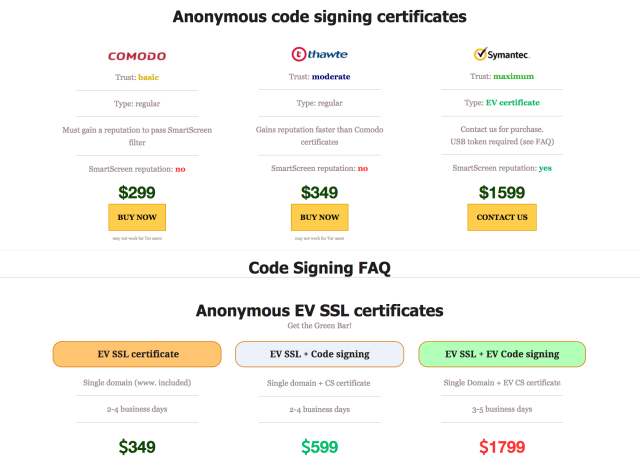
“In his advertisement, C@T explained that the certificates are registered under legitimate corporations and issued by Comodo, Thawte, and Symantec—the largest and most respected issuers,” Thursday’s report said. “The seller indicated that each certificate is unique and will only be assigned to a single buyer, which could be easily verified via HerdProtect.com. According to C@T, the success rate of payload installations from signed files increases by 30 to 50 percent, and he even admitted to selling over 60 certificates in less than six months.”
C@T’s business dwindled in coming years as other providers undercut his prices. One competing service provided a bare-bones code-signing certificate for $299. For $1,599, the service sold a signing certificate with extended validation—meaning it was issued to a corporate or business name that had been verified by the issuer. That premium price also ensured the certificate passed the SmartScreen validation check various Microsoft software perform to protect users against malicious apps. A package of fully authenticated Internet domains with EV SSL encryption and code signing capabilities could also be purchased for $1,799. The same service sold extended validation TLS certificates for websites starting at $349. A different C@T competitor sold highly vetted Class 3 certificates for $600.
Recorded Future
“According to the information provided by both sellers during a private conversation, to guarantee the issuance and lifespan of the products, all certificates are registered using the information of real corporations,” Barysevich wrote. “With a high degree of confidence, we believe that the legitimate business owners are unaware that their data was used in the illicit activities. It is important to note that all certificates are created for each buyer individually with the average delivery time of two to four days.”
Use of legitimate signing certificates to verify malicious apps and legitimate TLS certificates to authenticate domain names that distribute those apps can make security protections less effective. Recorded Future researchers provided one seller with an unreported remote access trojan and convinced the seller to sign it with a certificate that had been recently issued by Comodo. Only eight of the top AV providers detected an encrypted version of the trojan. Only two AV engines detected the same encrypted file when it was signed by the Comodo certificate.
“More disturbing results surfaced after the same test was conducted for a non-resident version of the payload,” Barysevich reported. “In that case, only six companies were capable of detecting an encrypted version, and only Endgame protection recognized the file as malicious.”
While Thursday’s report shows how simple it is to bypass many of the protections provided by code-signing requirements, Barysevich said that counterfeit certificates are likely to be used only in niche campaigns that target a small number of people or organizations.
“Although code signing certificates can be effectively used in widespread malware campaigns such as the distribution of banking trojan or ransomware, the validity of the certificate used to sign a payload would be invalidated fairly quickly,” he explained. “Therefore, we believe that the limited number of power-users specializing in more sophisticated and targeted campaigns, such as corporate espionage, is the main driving force behind the new service.”
Be the first to comment