As browser makers make it increasingly hard to exploit vulnerabilities in Adobe Flash and other plugins, hackers targeting diplomats in the Middle East tried a new approach this month: using Microsoft Office to remotely load Flash content that used a potent zero-day flaw to take control of computers.
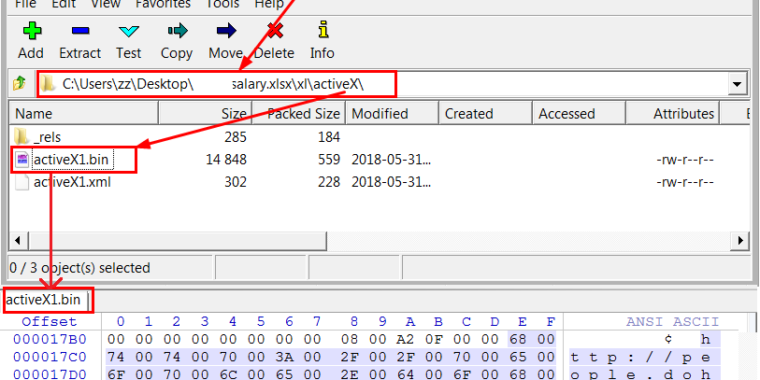
On Thursday, Adobe published a patch for the critical vulnerability, indexed as CVE-2018-5002. The stack-based buffer overflow was being triggered in an Office document that embedded a link to a Flash file stored on people.dohabayt.com. Once executed, the malicious file then downloaded a malicious payload from the same domain. That’s according to researchers from security firms Icebrg and Qihoo 360, which independently discovered the attacks and privately reported them to Adobe and wrote about it here and here.
Over the past few years, browser makers have begun to block Flash content by default, a change that has gone a long way to preventing drive-by attacks that exploit critical vulnerabilities in Adobe’s widely used media player. By contrast, at least some versions of Microsoft Office still download Flash with little or no user interaction, Icebrg CEO William Peteroy told Ars. To prevent downloads, users should ensure their installations prevent Flash from loading at all or at least don’t load Flash without explicit permission.
“The attack loads Adobe Flash Player from within Microsoft Office, which is a popular approach to Flash exploitation since Flash is disabled in many browsers,” Icebrg researchers Chenming Xu, Jason Jones, Justin Warner, and Dan Caselden wrote in Thursday’s blog post. Typically, a malicious Flash file is embedded directly into the document, making it possible that the exploit can be detected by antivirus providers. “Contrary to typical tactics, this attack uses a lesser-known feature that remotely includes the Flash content instead of directly embedding it within the document. Only XML wrappers selecting the Flash Player ActiveX control and an OLE Object supplying parameters are present.”
The benefit of the attack is that the document contains no exploit code, making it much harder to detect. Remotely downloading the exploit has an additional benefit: attackers can selectively serve exploits only to intended IP addresses rather than to anyone who happens to open the document. That allows attacks to remain undetected for longer periods of time.
At least some versions of Microsoft Office appear to block some forms of Flash. This support document from Microsoft says Office 2016 blocks Flash content but makes no reference to other versions. In May, Microsoft officials published a timeline for blocking Flash in Office 365 documents. Yet another document here seems to indicate that ActiveX controls are by default disabled, at least when a document is viewed in a protected mode.
In an advisory published Thursday, Microsoft provides guidance for turning off ActiveX in Office 2007 and Office 2010. Microsoft representatives weren’t immediately available on Thursday to explain precisely when Office documents do or don’t download Flash content or what end users can do to stop the behavior.
The malicious document is written in Arabic. When translated into English the title is “basic_salary.” Inside the document were salaries for a variety of positions related to embassies, including secretaries, ambassadors, and diplomats. Transmission of the exploits is protected by a custom cryptographic system that included a symmetric AES cipher and an asymmetric RSA cipher for transmitting the AES key. While the RSA cipher used a 512-bit key that can be cracked using powerful computers, the system nonetheless highlights the above-average capabilities of the attackers in preventing the attack from being easily discovered or analyzed.
The Icebrg researchers wrote:
The combination of a remotely included Flash exploit and asymmetric cryptography are particularly powerful counters against postmortem analysis. Once exploited, the only artifact residing on the victim’s system would be the initial lure document that only contains a URL. In that scenario, responders may look to network-packet captures to recreate the attack. However, without the victim’s randomly created private key, it would be impossible for responders to decrypt the attacker’s code and recover subsequent protected stages like the exploit or payload. In this scenario, responders’ only saving grace would be the use of a weak RSA modulus.
Over the past few years, security practitioners have increasingly advised that people uninstall the stand-alone Flash app and use a browser that blocks Flash content by default. The takeaway from Thursday’s research is that Office users should also be sure to block Flash content in documents, particularly those from unknown or untrusted parties. People who continue to use Flash should ensure they’re using version 30.0.0.113, available here.
Be the first to comment