Hackers have found a way to amplify distributed denial-of-service attacks by an unprecedented 51,000 times their original strength in a development that whitehats say could lead to new record-setting assaults that take out websites and Internet infrastructure.
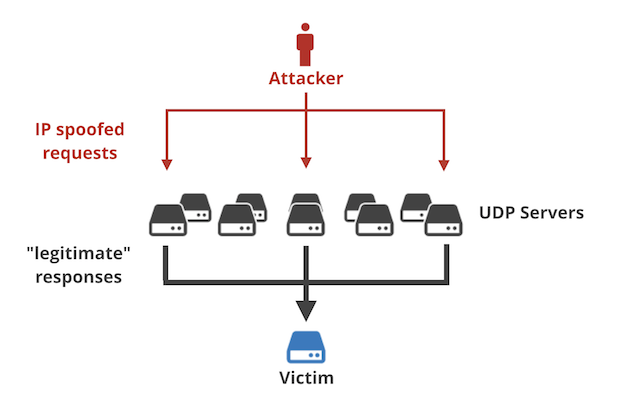
DDoS vandals have long intensified their attacks by sending a small number of specially designed data packets to publicly available services. The services then unwittingly respond by sending a much larger number of unwanted packets to a target. The best known vectors for these DDoS amplification attacks are poorly secured domain name system resolution servers, which magnify volumes by as much as 50 fold, and network time protocol, which increases volumes by about 58 times.
Cloudflare
On Tuesday, researchers reported attackers are abusing a previously obscure method that delivers attacks 51,000 times their original size, making it by far the biggest amplification method ever used in the wild. The vector this time is memcached, a database caching system for speeding up websites and networks. Over the past week, attackers have started abusing it to deliver DDoSes with volumes of 500 gigabits per second and bigger, DDoS mitigation service Arbor Networks reported in a blog post.
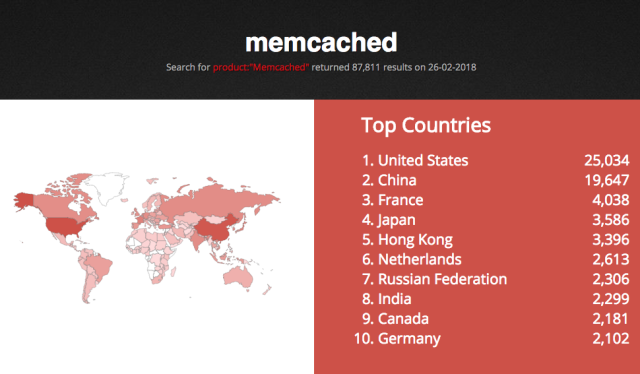
Officials at content delivery network Cloudflare, which reported the attacks here, said the attacks they’re seeing come from fewer than 6,000 memcached servers that are reachable on the Internet. Searches show there are more than 88,000 such servers, an indication there is potential for attacks to get much bigger.
“That’s an exceptionally large amplification factor,” said John Graham-Cumming, CTO of content delivery network Cloudflare, who added that that’s the biggest amplification factor he has ever seen. “I would expect over the next week or so we’ll see some very large attacks of over one terabit per second coming from it.”
DDoS mitigation service Incapsula estimates the magnification is a factor of 9,000 for memcached and 557 for NTP. It also estimated the number of memcache services available on the Internet over port 11211 at 93,000. Despite using different metrics, the figures support the contention that memcached offers an unprecedented factor of amplification and that there is a large pool of potential servers to abuse.
Some of the biggest publicly known DDoS attacks occurred in 2016. In September of that year, KrebsOnSecurity was taken out for days after receiving junk traffic volumes topping 620Gbps. Around the same time, OVH, a France-based Internet provider that’s a popular host for gaming servers, said it sustained attacks reaching 1.1Tbps and 901Gbps.
Those attacks were delivered by a then relatively new breed of botnet made up of hundreds of thousands of home routers and other so-called Internet of things devices. A variety of factors—including the ease of compromising the devices, the difficulty of securing them, and the sheer number of them—allowed miscreants to amass huge armies of DDoS pawns that could be harnessed in unison to deliver once unthinkable volumes of junk traffic.
Old-school DDoS
This month’s attacks abusing memcached servers harken back to older DDoS attacks that don’t require massive botnets. Memcached servers typically have plenty of bandwidth available to them. Combined with the 51,000-fold amplification they provide, DDoSers need only a handful of devices to deliver an initial payload. That makes the technique available to a much larger group of people, rather than to just those with control over a large botnet.
“The potential collateral impact of memcached reflection/amplification DDoS attacks can be highly significant, as these attacks exhibit high reflection/amplification ratios and leverage server-class reflectors/amplifiers which typically feature high-bandwidth access-links and which reside in Internet Data Centers (IDCs) with high-speed upstream transit links,” Roland Dobbins, principal engineer on Arbor’s Security Engineering & Response Team, wrote in Tuesday’s post.
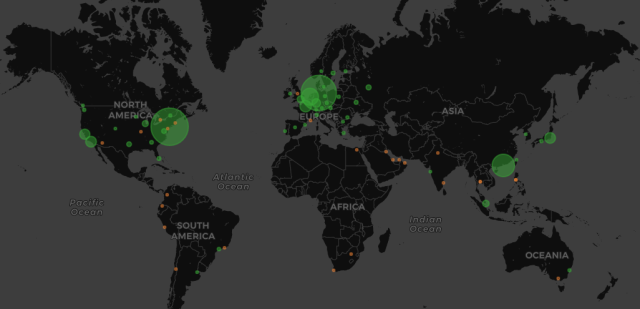
The attacks work because a variety of networks is exposing memcached servers to the Internet in their default unsecured configuration. Generally speaking, memcached systems should be reachable only on local networks and should be kept securely behind a firewall. So far, attacks have come from slightly more than 5,700 unique IP addresses, mostly in North America and Europe.
Cloudflare
“I suspect that most of these memcached servers don’t need to be on the public Internet,” Graham-Cumming said. “It’s just a mistake.” He said his concern about worsening attacks is fueled by the previously mentioned availability of more than 88,000 poorly secured memcached servers, as measured by the Shodan search engine.
Cloudflare
To harness the huge attack potential of the servers, DDoSers send them a relatively small number of UDP-based packets that have been manipulated to appear as if they were sent by the intended target. The memcached servers respond by sending the target the massive response. The attacks once again underscore the public nuisance that results from service providers that still permit UDP packets to be spoofed to falsify the true sender.
Both Cloudflare and Arbor Networks are advising network providers that deploy memcached servers to disable UDP support when possible. In many cases, TCP-based traffic suffices. In all cases, servers should be firewalled from the Internet.
Be the first to comment